Introduction
Session Replay Attacks are a significant security threat where attackers can hijack and replay user sessions to gain unauthorized access to sensitive data. In Laravel, which is a popular PHP framework, ensuring your session management is secure is crucial to protect against such vulnerabilities.
In this blog post, we'll dive into what Session Replay Attacks are, how they work, and practical steps to prevent them in Laravel applications. We will also show how to use the Website Vulnerability Scanner tool to ensure your website is safe from session-related vulnerabilities.
What is a Session Replay Attack?
A Session Replay Attack occurs when an attacker captures the session token of a legitimate user and reuses it to impersonate that user. This can lead to unauthorized access to user accounts, theft of sensitive information, or even account takeover.
Attackers often capture session tokens by exploiting flaws in the application, such as using unencrypted cookies or predictable session IDs.
How Session Replay Attacks Work
Session Hijacking: An attacker intercepts the session token (usually stored in cookies) by using various methods such as man-in-the-middle (MITM) attacks, browser vulnerabilities, or social engineering.
Replay Attack: After capturing the session token, the attacker uses it to impersonate the victim by sending the same token in a request to the server.
Accessing Sensitive Data: The attacker can now access the victim’s account, view private data, make unauthorized transactions, or perform any other action that the user could.
Steps to Prevent Session Replay Attacks in Laravel
Laravel provides built-in features that can help protect your application from Session Replay Attacks. Below are the key techniques to secure session management in Laravel.
1. Use HTTPS (SSL/TLS) Everywhere
Ensure that your Laravel application enforces HTTPS (SSL/TLS) for all pages, especially those involving authentication or sensitive data. This will encrypt session tokens and protect them from being intercepted during transmission.
In Laravel, you can enforce HTTPS by setting the APP_URL to use https in your .env file:
APP_URL=https://yourwebsite.com
Also, ensure your cookies are only sent over secure connections:
'secure' => env('SESSION_SECURE_COOKIE', true),
2. Set SameSite Attribute for Cookies
Laravel supports setting the SameSite attribute for cookies, which helps prevent cross-site request forgery (CSRF) and session replay attacks. The SameSite attribute ensures that cookies are only sent with requests originating from the same site.
Set the SameSite attribute in config/session.php:
'same_site' => 'strict', // or 'lax'
This ensures that session cookies will only be sent in requests from the same domain.
3. Regenerate Session ID on Sensitive Actions
To make it harder for attackers to replay session tokens, you should regenerate the session ID after any sensitive actions, such as logging in or changing account settings.
Use the regenerate method provided by Laravel to regenerate the session ID:
public function login(Request $request)
{
// Perform login logic...
$request->session()->regenerate();
}
Regenerating the session ID ensures that attackers can't reuse a session token after it’s been changed.
4. Implement Two-Factor Authentication (2FA)
By implementing Two-Factor Authentication (2FA), you can further protect users’ accounts. Even if an attacker manages to hijack a session, they would still need the second factor (like an OTP) to gain access.
In Laravel, you can implement 2FA using packages like Google2FA or Laravel Fortify.
composer require pragmarx/google2fa-laravel
Testing Your Laravel Application for Session Vulnerabilities
You can use the free Website Security Scanner tool to scan your Laravel application for potential vulnerabilities related to session management. The tool will help you identify if your application is exposed to session replay attacks and suggest fixes.
Here’s how you can use the tool:
- Visit the tool at https://free.pentesttesting.com/.
- Enter your website URL.
- Run the scan and review the results.
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
Code Example: Secure Session Management in Laravel
Here’s a practical example of implementing secure session management in Laravel:
// Middleware to ensure secure session handling
public function handle($request, Closure $next)
{
// Regenerate session ID after login
if ($request->isMethod('post')) {
session()->regenerate();
}
return $next($request);
}
This middleware ensures that the session ID is regenerated whenever the user performs a POST request, adding another layer of security against session replay attacks.
Conclusion
Session Replay Attacks pose a serious security threat, but with the right precautions, you can protect your Laravel application. By enforcing HTTPS, setting cookie attributes, regenerating session IDs, and implementing 2FA, you can significantly reduce the risk of such attacks.
Don't forget to use the Website Security Checker tool to test your application's vulnerability and improve its security posture.
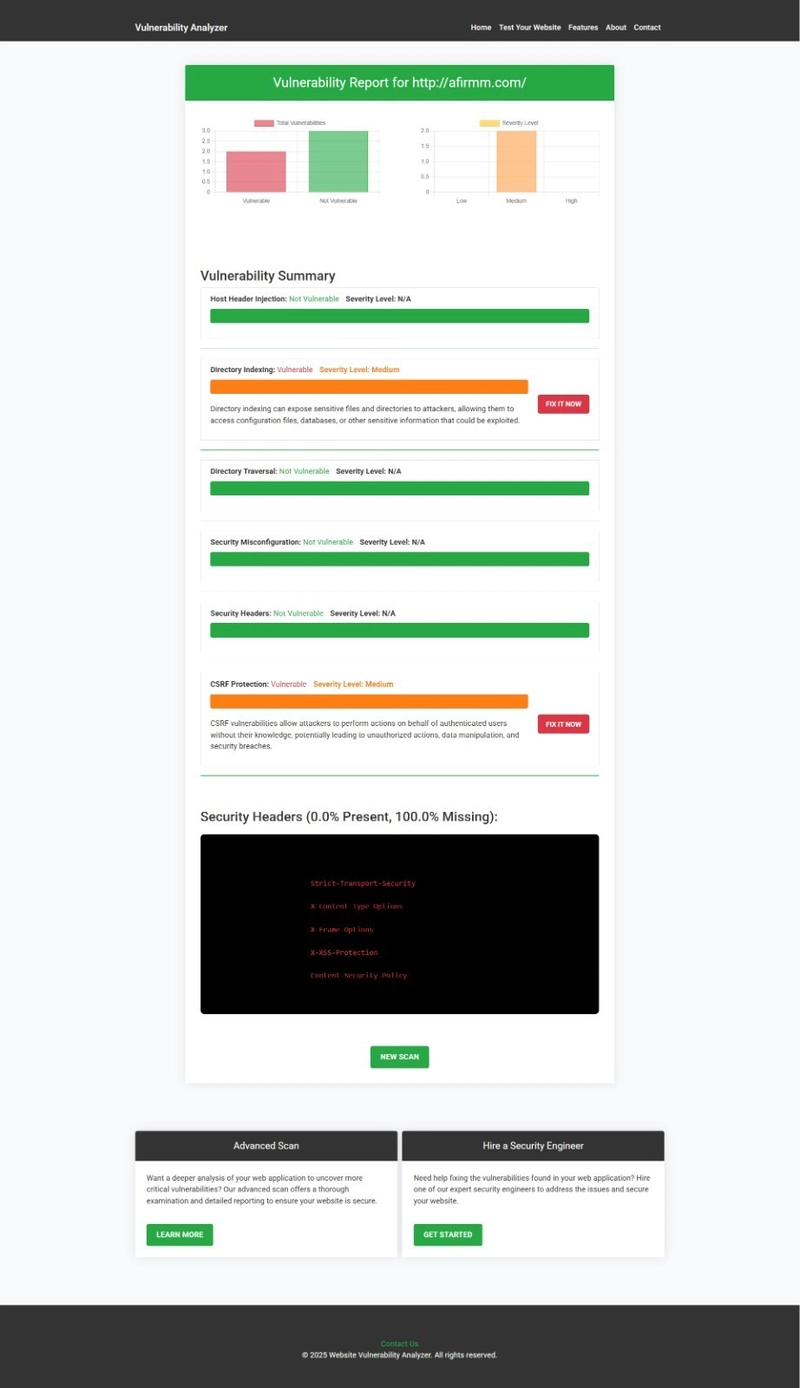 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
For more security tips and in-depth guides, visit the Pentest Testing Corp Blog.





Top comments (0)