In today’s threat landscape, securing data in transit is not optional—it’s a necessity. One of the most dangerous and often overlooked vulnerabilities in web applications is the Man-in-the-Middle (MitM) attack. In this blog post, we’ll dive deep into how MitM attacks occur in Symfony applications, how to exploit and prevent them with real code examples, and how to leverage automated tools to ensure robust protection.
🔗 Bonus: We’ll show you how to test your Symfony site using our free Website Security Scanner tool.
💀 What is a Man-in-the-Middle (MitM) Attack?
A MitM attack occurs when an attacker secretly intercepts and potentially alters communications between two parties—typically between a user and a website. This allows them to steal sensitive data like login credentials, session tokens, and even inject malicious responses.
Common MitM Techniques
- ARP spoofing on local networks
- DNS poisoning
- HTTPS stripping
- Fake Wi-Fi hotspots
🛠 How Symfony Apps Can Be Vulnerable
Symfony, by default, follows modern security practices, but developers often misconfigure HTTP transport or overlook proper TLS enforcement, especially in development or staging environments.
Here’s an example of insecure Symfony configuration:
# config/packages/framework.yaml
framework:
http_method_override: true
trusted_proxies: ~
session:
cookie_secure: auto # should be 'true' in production
👉 MitM attacks often exploit missing Strict-Transport-Security headers and unsecured cookies.
🔐 How to Prevent MitM Attacks in Symfony
1. Always Force HTTPS
Make sure your Symfony app redirects all traffic to HTTPS.
Add this to your .htaccess or Nginx config:
RewriteCond %{HTTPS} off
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
For Symfony, configure secure URLs in routes:
# config/packages/security.yaml
access_control:
- { path: ^/admin, roles: ROLE_ADMIN, requires_channel: https }
2. Enable HSTS (Strict Transport Security)
HSTS ensures that the browser never communicates with your site over HTTP.
Add this response header in Symfony via an event subscriber:
// src/EventSubscriber/SecurityHeaderSubscriber.php
namespace App\EventSubscriber;
use Symfony\Component\EventDispatcher\EventSubscriberInterface;
use Symfony\Component\HttpKernel\Event\ResponseEvent;
class SecurityHeaderSubscriber implements EventSubscriberInterface
{
public static function getSubscribedEvents()
{
return [ResponseEvent::class => 'onKernelResponse'];
}
public function onKernelResponse(ResponseEvent $event)
{
$event->getResponse()->headers->set('Strict-Transport-Security', 'max-age=31536000; includeSubDomains; preload');
}
}
👉 Don’t forget to register your domain for preload at https://hstspreload.org.
🧪 Real-World Exploit: Simulating MitM via HTTPS Stripping
Let’s simulate an insecure login page in Symfony:
// src/Controller/LoginController.php
public function login(Request $request): Response
{
$username = $request->request->get('username');
$password = $request->request->get('password');
// ⚠️ Data sent over HTTP without TLS
// An attacker can intercept this
return new Response('Login attempted');
}
If this form is submitted over HTTP, a packet sniffer (like Wireshark) can easily capture the username and password. This is a textbook MitM scenario.
✅ Fix: Enforce HTTPS and implement CSRF + input validation + TLS pinning on mobile clients.
🧪 Try Our Free Website Vulnerability Scanner Tool
To make life easier, we built a free Website Vulnerability Scanner tool to detect misconfigurations that may lead to MitM attacks and other OWASP vulnerabilities.
🖼️ Free Website Security Checker Tool Screenshot:
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
🖼️ Security Report Screenshot to check Website Vulnerability
It checks for:
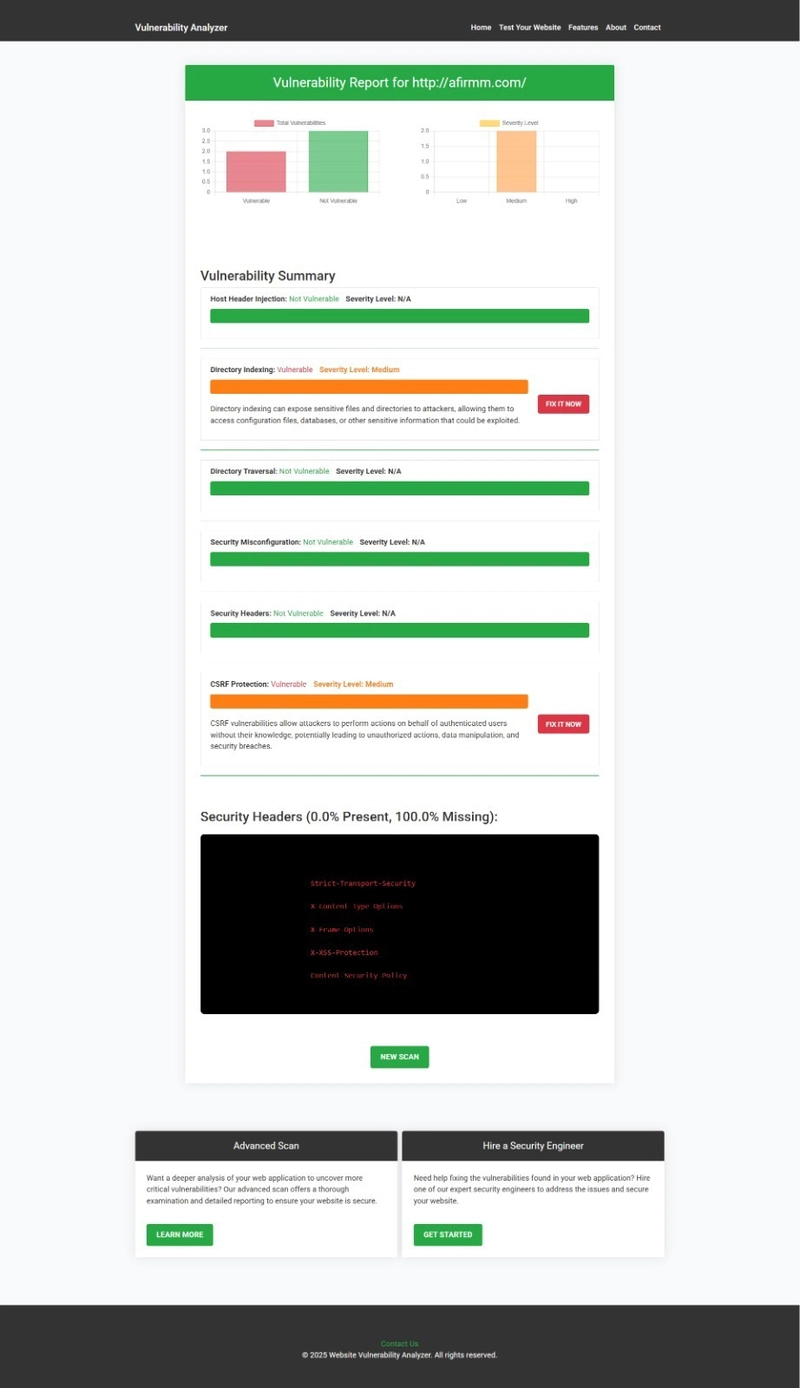 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
- Insecure HTTP endpoints
- Missing HSTS headers
- Cookie security flags
- TLS certificate issues
Run a test now at 👉 https://free.pentesttesting.com
💼 Secure Your Symfony App Professionally
If you’re looking for comprehensive, manual, and automated testing of your Symfony web application, we offer full-stack penetration testing services.
🔐 Check out our Web App Penetration Testing Services:
👉 https://www.pentesttesting.com/web-app-penetration-testing-services/
We test for:
- TLS/SSL weaknesses
- Session hijacking
- Insecure authentication
- Business logic flaws
—
🧠 Learn More on Our Blog
We frequently publish technical walkthroughs, exploit deep-dives, and prevention strategies on our blog. Check it out:
🔍 Pentest Testing Corp Blog:
👉 https://www.pentesttesting.com/blog/
—
📬 Stay Updated
Subscribe to our LinkedIn newsletter for weekly updates on cybersecurity vulnerabilities, secure coding, and tool releases:
📩 Subscribe on LinkedIn
👉 https://www.linkedin.com/build-relation/newsletter-follow?entityUrn=7327563980778995713
—
🧾 Final Thoughts
MitM attacks are stealthy, but not unstoppable. By understanding how they work and proactively configuring your Symfony app with secure headers, forced HTTPS, and constant testing via tools like ours for Web app security tests, you can ensure that your users’ data stays safe in transit.
Got questions or want help reviewing your Symfony app? Reach out or subscribe to stay in the loop.
Happy hacking (the good kind)! 🔐





Top comments (0)