Symfony is a powerful and widely-used PHP framework for building robust web applications and APIs. However, as with any framework, its improper use can introduce security vulnerabilities — especially in APIs, which are common attack targets. In this article, we’ll explore common API vulnerabilities found in Symfony apps, how they occur, and how to fix them using code examples.
🔒 We’ll also show how to scan your Symfony-based website or API with our free Website Security Scanner tool.
Why Symfony APIs Are Vulnerable
Symfony provides a lot of flexibility and extensibility, but developers often make mistakes like:
- Exposing sensitive routes
- Improper input validation
- CSRF and CORS misconfigurations
- Broken authentication logic
- Insecure serialization/deserialization
Let’s dive into some of these.
1. Insecure Route Exposure
🛑 Problem:
Developers may accidentally expose sensitive internal API routes.
🔐 Vulnerable Code:
// src/Controller/Api/InternalController.php
/**
* @Route("/api/admin/data", name="admin_data")
*/
public function getAdminData()
{
return new JsonResponse(['secret' => 'internal only']);
}
🔍 Issue:
This endpoint should not be public. But Symfony's routing makes it easily exposed unless access control is enforced.
✅ Fix:
Use Symfony’s access_control in security.yaml:
# config/packages/security.yaml
access_control:
- { path: ^/api/admin, roles: ROLE_ADMIN }
2. Missing Input Validation & Mass Assignment
🛑 Problem:
Symfony Forms or direct JSON input can result in mass assignment.
🔐 Vulnerable Code:
$data = json_decode($request->getContent(), true);
$user = new User();
$form = $this->createForm(UserType::class, $user);
$form->submit($data); // Risk of mass assignment!
✅ Fix:
Use DTOs and manually map only allowed fields:
// src/DTO/UserDTO.php
class UserDTO {
public string $email;
public string $name;
}
// Controller
$dto = new UserDTO();
$form = $this->createForm(UserDTOType::class, $dto);
$form->submit($data);
// Then map fields manually to Entity
$user->setEmail($dto->email);
$user->setName($dto->name);
3. Broken Authentication Logic
🛑 Problem:
Using default Symfony user serialization without considering token-based auth may leak sensitive data.
🔐 Vulnerable Code:
return $this->json($user);
✅ Fix:
Use a custom serializer group or response structure.
return $this->json([
'id' => $user->getId(),
'email' => $user->getEmail()
]);
And configure serialization groups:
// src/Entity/User.php
/**
* @Groups("public")
*/
private $email;
4. CSRF Tokens in API Forms
🛑 Problem:
CSRF tokens are often unnecessary in APIs (esp. JSON APIs) and can break functionality.
✅ Fix:
Disable CSRF in forms used in APIs:
$form = $this->createForm(UserType::class, $user, [
'csrf_protection' => false,
]);
5. CORS Misconfiguration
Misconfigured CORS headers can allow unauthorized sites to interact with your API.
✅ Fix:
Install NelmioCorsBundle:
composer require nelmio/cors-bundle
Configure securely:
# config/packages/nelmio_cors.yaml
nelmio_cors:
defaults:
allow_credentials: false
allow_origin: ['https://yourdomain.com']
allow_headers: ['Content-Type', 'Authorization']
allow_methods: ['GET', 'POST', 'PUT', 'DELETE']
🔧 Scan Your Symfony App for Free
Use our Free Website Security Checker to instantly find vulnerabilities in your Symfony website or API.
📸 Screenshot: Free Website Vulnerability Scanner UI
🖼️ Homepage of our Website Vulnerability Scanner tool
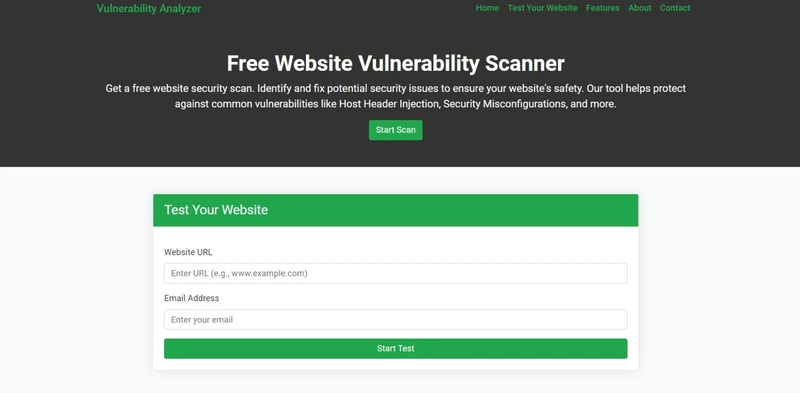 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
📸 Screenshot: Vulnerability Assessment Report
🖼️ Example of a vulnerability scan report generated by our free tool to check Website Vulnerability
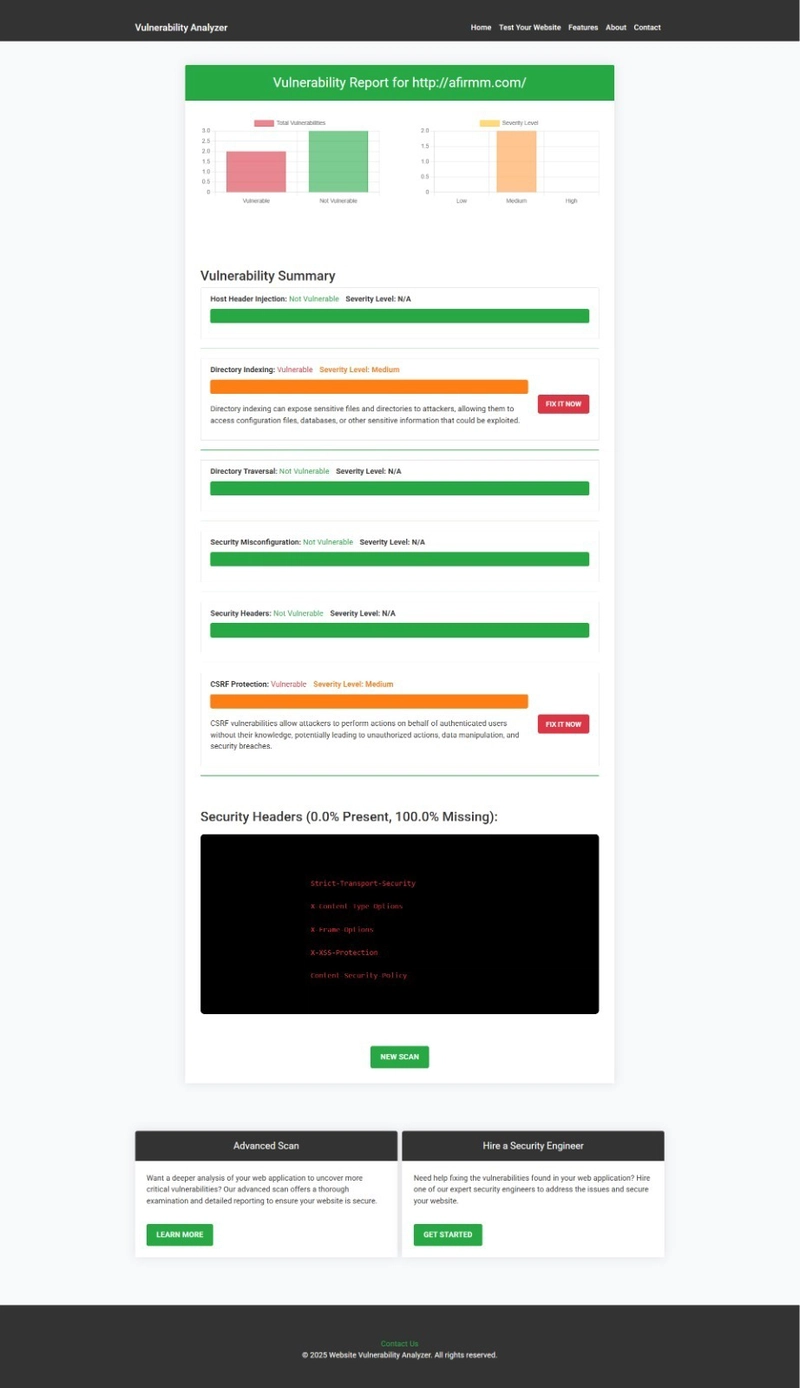 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
🧠 Learn More on Our Blog
Want deeper insights into web app security and threat analysis? Visit our cybersecurity blog at Pentest Testing Corp.
🚀 New Service: Web App Penetration Testing
If you’re looking for expert manual testing on your Symfony API or web application, explore our professional service here:
👉 Web App Penetration Testing Services
We provide tailored penetration testing with comprehensive reporting, risk assessments, and mitigation guidance.
📬 Stay Informed — Join Our Newsletter
Get the latest on API security, Symfony, Laravel, and web vulnerabilities by subscribing to our newsletter on LinkedIn:
🧪 Final Thoughts
Symfony is powerful but demands secure coding practices. API vulnerabilities can sneak in through simple oversights. By understanding common pitfalls — and using tools like ours for a Website Security check — you can proactively secure your APIs and safeguard your users.
📢 Share this post, leave feedback, and let us know what frameworks you'd like us to cover next!



Top comments (0)