Insufficient Logging and Monitoring in Symfony is one of the most overlooked yet dangerous vulnerabilities in web application security. Without proper logging mechanisms, threat actors can exploit your system without leaving a trace, leading to data breaches, prolonged attacks, and compliance issues.
In this blog post, you'll learn:
- What Insufficient Logging and Monitoring means
- How it impacts Symfony applications
- Real-world coding examples of weak and secure implementations
- How to detect it using our free tool: free Website Security Scanner
- How to fix and monitor your Symfony app effectively
🔍 What is Insufficient Logging and Monitoring in Symfony?
This vulnerability occurs when a Symfony application fails to:
- Log critical user actions (e.g., logins, password changes)
- Monitor logs for suspicious patterns
- Alert administrators in real-time
Without logs, incident response becomes nearly impossible.
💥 The Risks of Poor Logging in Symfony
- Attackers can brute-force passwords without detection
- Malicious users can exfiltrate data unnoticed
- You risk violating GDPR, HIPAA, or PCI DSS if forensic logs are missing
- No clear trail for debugging and incident investigation
⚠️ Real-World Example of Vulnerable Symfony Logging
Here’s a common mistake many Symfony developers make—using default error logging without customizing log levels or channels:
❌ Bad Practice:
// src/Controller/SecurityController.php
public function login(Request $request, LoggerInterface $logger)
{
// Only logs info; misses failed attempts
$logger->info('User login attempt');
// Authentication logic
}
This log won't catch failed logins or anomalies like multiple attempts from the same IP.
✅ Best Practice:
public function login(Request $request, LoggerInterface $logger)
{
$user = $request->get('username');
// Log all login attempts with severity
try {
// Authentication logic
$logger->info("Login success for user: $user");
} catch (AuthenticationException $e) {
$logger->warning("Login failure for user: $user from IP: " . $request->getClientIp());
throw $e;
}
}
💡 Tip: Use monolog.yaml to set proper log levels and rotate logs securely.
🔐 Enabling Real-Time Monitoring with Symfony + Monolog
Symfony uses Monolog as the default logging library. Here's how to set up real-time alerts:
📦 In config/packages/monolog.yaml:
monolog:
handlers:
main:
type: fingers_crossed
action_level: warning
handler: nested
nested:
type: stream
path: "%kernel.logs_dir%/%kernel.environment%.log"
level: debug
slack:
type: slack
token: '%env(SLACK_TOKEN)%'
channel: '#security-alerts'
level: critical
This will push critical security alerts directly to Slack. You can also use third-party services like Sentry or Elastic Stack for log correlation and visualization.
🧪 Scan Your Symfony App for Logging Vulnerabilities
Our free Website Vulnerability Scanner Tool will help you:
- Scan your Symfony app for missing logs
- Detect brute force attempts or enumeration
- Generate an actionable report for DevSecOps teams
📸 Screenshot of the Website Vulnerability Scanner tool homepage
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
📸 Screenshot of a vulnerability report generated by our free tool to check Website Vulnerability
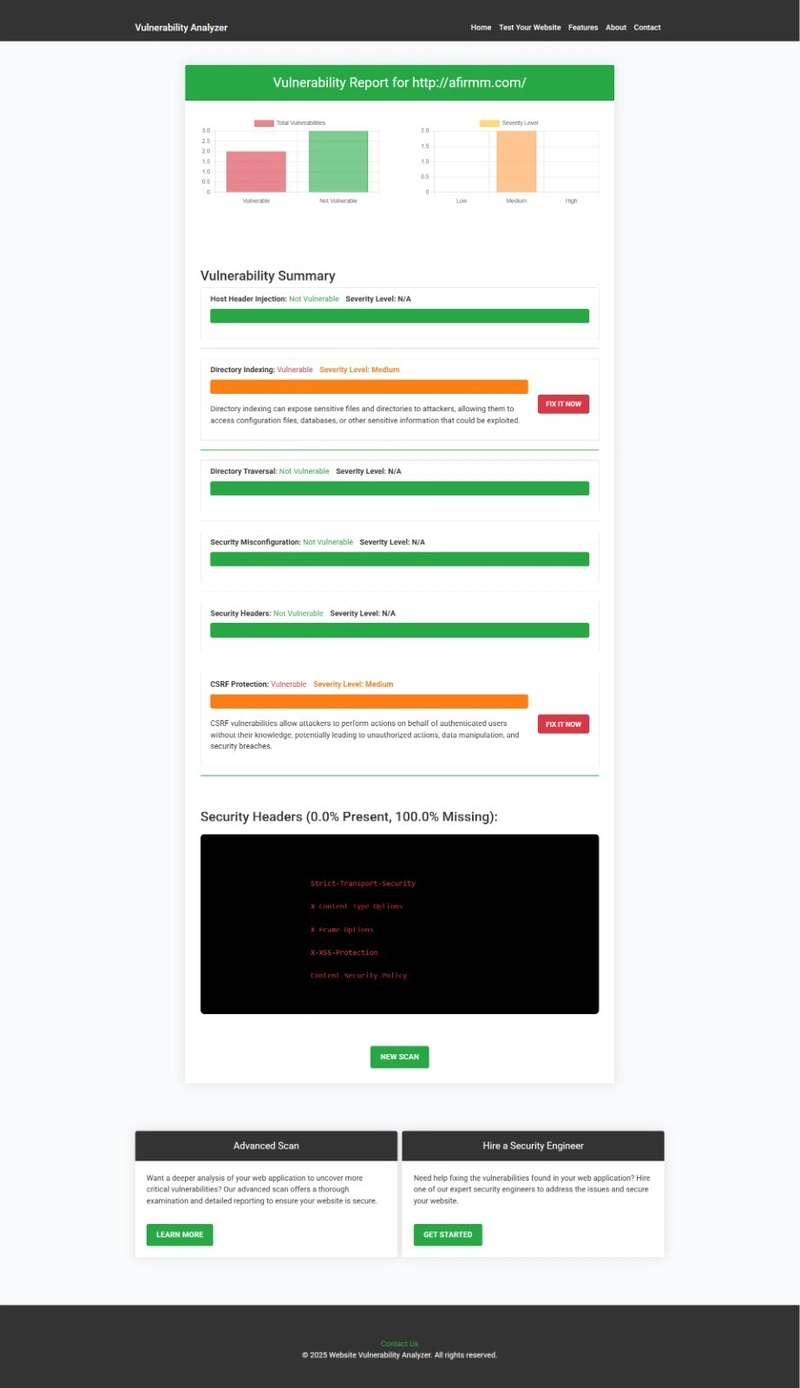 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
📘 More Secure Symfony Articles
Want more insights on Symfony security? Check out our blog:
🔗 Pentest Testing Corp.
Some related reads:
💼 Upgrade Your Security With Pro-Level Penetration Testing
If you're serious about your Symfony application's security posture, consider our professional services:
🔐 Web Application Penetration Testing Services
Our certified experts will:
- Simulate real-world attacks
- Uncover security misconfigurations and logic flaws
- Deliver a remediation-focused report
📩 Stay Updated — Join Our Newsletter
Subscribe to our LinkedIn newsletter for more security tips, tool updates, and case studies:
🏁 Final Thoughts
Insufficient Logging and Monitoring in Symfony is not just a coding flaw—it's a business risk. By implementing proper logs, integrating alerting systems, and running regular security scans, you take a huge step toward resilience.
Try our tool today 👉 free.pentesttesting.com
💬 Questions or suggestions? Drop them in the comments.






Top comments (0)