Many developers have heard about SafeLine WAF and its strong protection capabilities. But unless you've seen it in action, it's hard to know just how well it works.
So we put it to the test—specifically against SQL injection, one of the most common and dangerous web vulnerabilities.
This post walks you through a simple demo and shows how SafeLine handles SQL injection attacks, even when the underlying application is vulnerable.
Understanding SQL Injection
SQL injection targets applications that use SQL queries to interact with a database. When user input is not properly sanitized, attackers can inject malicious SQL code to access or manipulate sensitive data.
For this test, we used a vulnerable demo environment called DVWA (Damn Vulnerable Web Application)—you can easily set it up for your own experiments.
Let’s start with a simple input:
Input: 1
Based on the output, it seems the backend query could be something like:
SELECT first_name, last_name FROM users WHERE user_id = '$id';
In real-world scenarios, if the application fails to properly escape input, this is an easy entry point for SQL injection.
Simulating an Attack
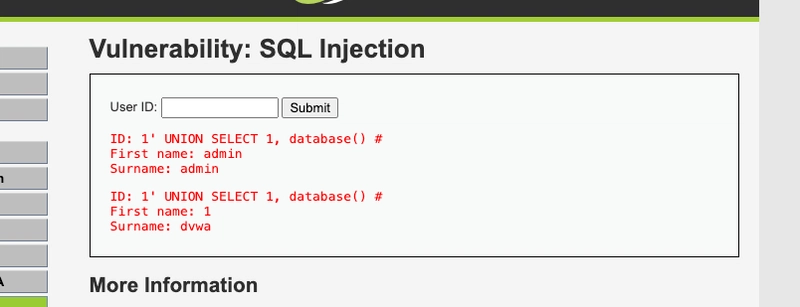
Let’s try to extract the current database name using a classic injection payload:
Input: 1' UNION SELECT 1, database() #
This works. We successfully retrieve the database name, proving that the injection succeeded. But we won’t go deeper into exploitation here—this is just for demonstration purposes.
Introducing SafeLine WAF
Now, let’s route this same vulnerable app through SafeLine WAF. Configuration is simple—just set up the target site through the SafeLine panel and point your traffic through it.
Then, try the same attack input again:
Input: 1' UNION SELECT 1, database() #
✅ Blocked.
SafeLine immediately intercepts the request. The attack never reaches the backend, and no sensitive data is exposed. The user sees a generic error page—no clue about what's going on behind the scenes.
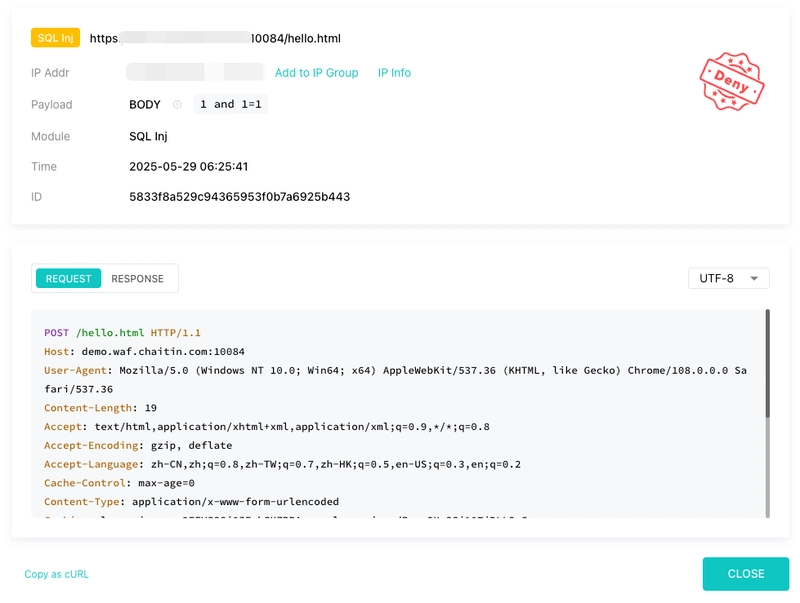
Logs and Analysis
You can check the interception logs inside the SafeLine dashboard.
Final Thoughts
This was a basic example, but it highlights a key point:
Even if your app isn’t perfectly secure, using a WAF adds a critical layer of protection.
SafeLine is a solid, easy-to-deploy solution that acts as a smart first line of defense. For developers who want peace of mind without enterprise-level overhead, it’s absolutely worth a try.
🔗 Useful Links:








Top comments (0)