A Real-World Banking System Using useradd, chmod, ACLs, systemd, and More!
🚀 What if you could manage 10,000 bank customers using only Linux commands?
In this hands-on project, you’ll simulate a secure banking portal that handles users, enforces privacy, encrypts backups, and even triggers alerts on suspicious activity.
🏦 Scenario: You’re the Sysadmin for a Bank
Your Mission:
- Give employees admin access (but safely).
- Ensure customers can only access their data.
- Maintain daily encrypted transaction logs.
- Detect fraudulent logins in real time.
Let’s turn a regular Linux machine into a secure bank portal. 💻💸
## 📑 Table of Contents
- 🔧 Step 1: Create Users & Groups
- 💰 Step 2: Secure the Banking Directories
- 🔍 Step 3: Monitor Suspicious Activity
- ⏰ Step 4: Automate Encrypted Daily Backups
- 🏧 Step 5: Simulate a Customer Login
- 💻 Demo: Bank Customer Login Simulation
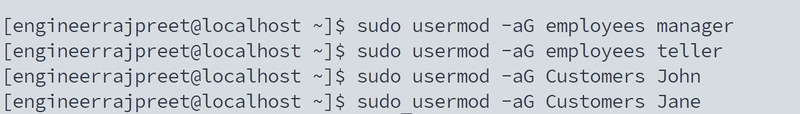
🔧 Step 1: Create Users & Groups
🛠 Tools: useradd, usermod, groups
# Employees and Customers
Similarly, Create Groups, Assign Users to groups
sudo groupadd employees
sudo groupadd customers
sudo usermod -aG employees manager teller
sudo usermod -aG customers john jane
✅ Why?
- Groups control permissions.
- Customers can’t peek into each other’s data.
- Employees can manage transactions but not compromise privacy.
💰 Step 2: Secure the Banking Directories
🛠 Tools: mkdir, chmod, chown, setfacl
# Let employees read but not write customer data
![]()
🔒 Why?
- chmod 700: Only the customer can access their folder.
- setfacl: Employees can view but not edit customer files.
- /bank/transactions: Editable only by employees.
🔍 Step 3: Monitor Suspicious Activity
🛠 Tools: grep, journalctl, find
# Failed logins (fraud detection)
sudo grep "Failed password" /var/log/auth.log
Similarly, You can Check Suspicious activity by these commands:
# Audit sudo usage
sudo journalctl -q | grep "sudo.*COMMAND"
# Detect changes in the last hour
sudo find /bank -type f -mmin -60 -ls
🚨 Why?
- Spot brute-force attacks and insider misuse.
- Know who’s using sudo, when, and for what.
- Track recent changes to sensitive files.
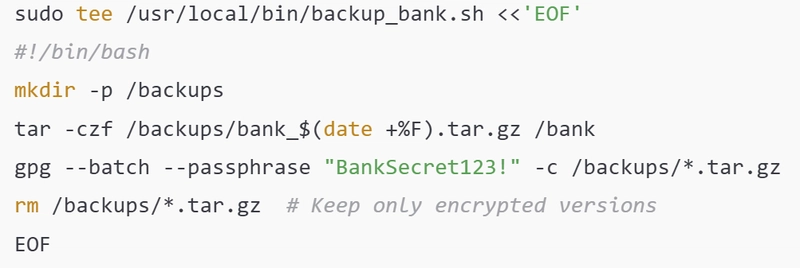
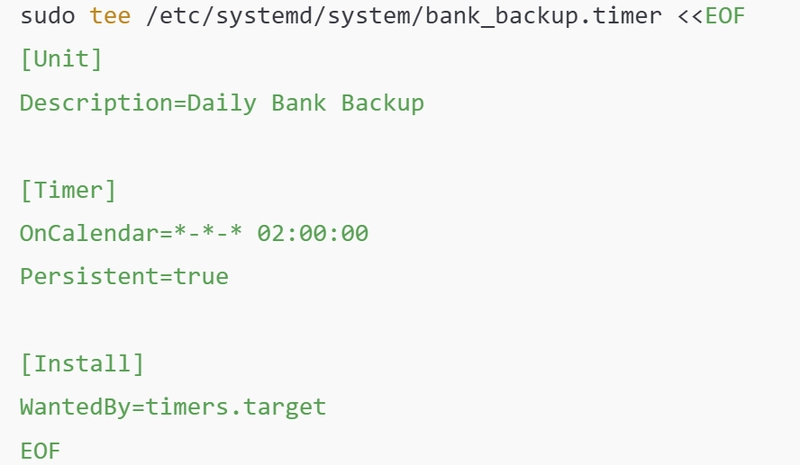
⏰ Step 4: Automate Encrypted Daily Backups
🛠 Tools: systemd, tar, gpg, cron
# 1. Backup script
# 2. Make executable
# 3. Systemd timer
# 4. Start the timer
🗝️ Why?
- Protects data even if the system is breached.
- Systemd ensures it runs reliably—even after reboot.
🏧 Step 5: Simulate a Customer Login
💻 Demo: Bank Customer Login Simulation
📘 Conclusion
With just a few Linux commands, you've built a:
✅ Secure multi-user bank portal
✅ Automated encrypted backups
✅ Real-time monitoring system
💡 Want to take it further? Add:
- Email alerts for suspicious logins
- Web frontend using Apache/Nginx
- PostgreSQL for storing balances
#30DaysLinuxChallenge #CloudWhisler
DevOps #Linux #RHCSA #Opensource #AWS #CloudComputing
Catch out by My LinkedIn profile
https://www.linkedin.com/in/rajpreet-gill-4569b4161/












Top comments (1)
been messing with user permissions before but tbh never thought about banking setups like this, feels like i'm missing a trick