Sensitive data exposure is one of the most critical and common web security risks today. In Symfony-based applications, misconfigurations and insecure coding practices often leave sensitive information like API keys, user data, and credentials vulnerable to attackers.
In this article, we’ll walk through what sensitive data exposure means, how it affects Symfony applications, and show you real code examples of insecure and secure implementations. Plus, we’ll share how to scan your website using our free website vulnerability scanner online.
🔍 What Is Sensitive Data Exposure?
Sensitive data exposure occurs when an application fails to protect critical information, such as:
- Passwords
- Session tokens
- Credit card numbers
- Health data
- Personal identifiable information (PII)
Even if this data isn't actively stolen, its mere availability via logs, error messages, or weak encryption can lead to devastating breaches.
🧪 Example 1: Accidental Debug Mode Enabled
One of the most common Symfony issues is leaving debug mode turned on in production.
❌ Insecure Code:
# config/packages/dev/web_profiler.yaml
web_profiler:
toolbar: true
intercept_redirects: false
If this config leaks into production, stack traces, database details, and environment variables can be publicly exposed.
✅ Secure Practice:
# config/packages/prod/web_profiler.yaml
web_profiler:
toolbar: false
intercept_redirects: false
Always disable debug mode and profiler in production environments.
🔐 Example 2: Exposing Sensitive Config in .env File
Symfony uses .env files for environment variables. Accidentally committing them to version control is a massive risk.
❌ Insecure:
DATABASE_URL=mysql://root:root@127.0.0.1:3306/mydb
MAILER_DSN=smtp://username:password@mailserver:25
If .env gets pushed to GitHub or leaked elsewhere, attackers gain access to your whole app.
✅ Secure Approach:
- Add
.envto.gitignore - Use environment variables in the server (e.g., AWS, Docker secrets)
- Use Symfony Vault or dotenv safely
📝 Example 3: Sensitive Data in Logs
Symfony logs every request by default. If not configured, it may log passwords, tokens, or session data.
❌ Risky Logging:
$logger->info('User login: ', ['username' => $user, 'password' => $password]);
✅ Secure Logging:
$logger->info('User login attempted.', ['username' => $user]);
// Never log passwords or tokens.
Use $context wisely and filter out sensitive keys.
🔧 Example 4: Weak or No Encryption
Storing passwords or sensitive data without hashing or encryption is fatal.
❌ Insecure Password Storage:
// Plaintext passwords – NEVER do this!
$user->setPassword($request->get('password'));
✅ Secure Symfony Password Hashing:
$password = $passwordHasher->hashPassword($user, $request->get('password'));
$user->setPassword($password);
Symfony uses bcrypt or argon2i hashing by default — always hash and never store raw values.
🛠️ How to Prevent Sensitive Data Exposure
- Disable debug mode in production
- Add
.envand secrets to.gitignore - Use HTTPS for all environments
- Avoid logging sensitive data
- Hash passwords securely
- Regularly scan your website for exposure vulnerabilities
To help you assess your current security posture, we’ve created a Free Website Vulnerability Scanner.
🖼️ Screenshot of the website vulnerability scanner tool page:
 Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of the free tools webpage where you can access security assessment tools.
🖼️ Screenshot of a vulnerability assessment report generated by our tool to check Website Vulnerability:
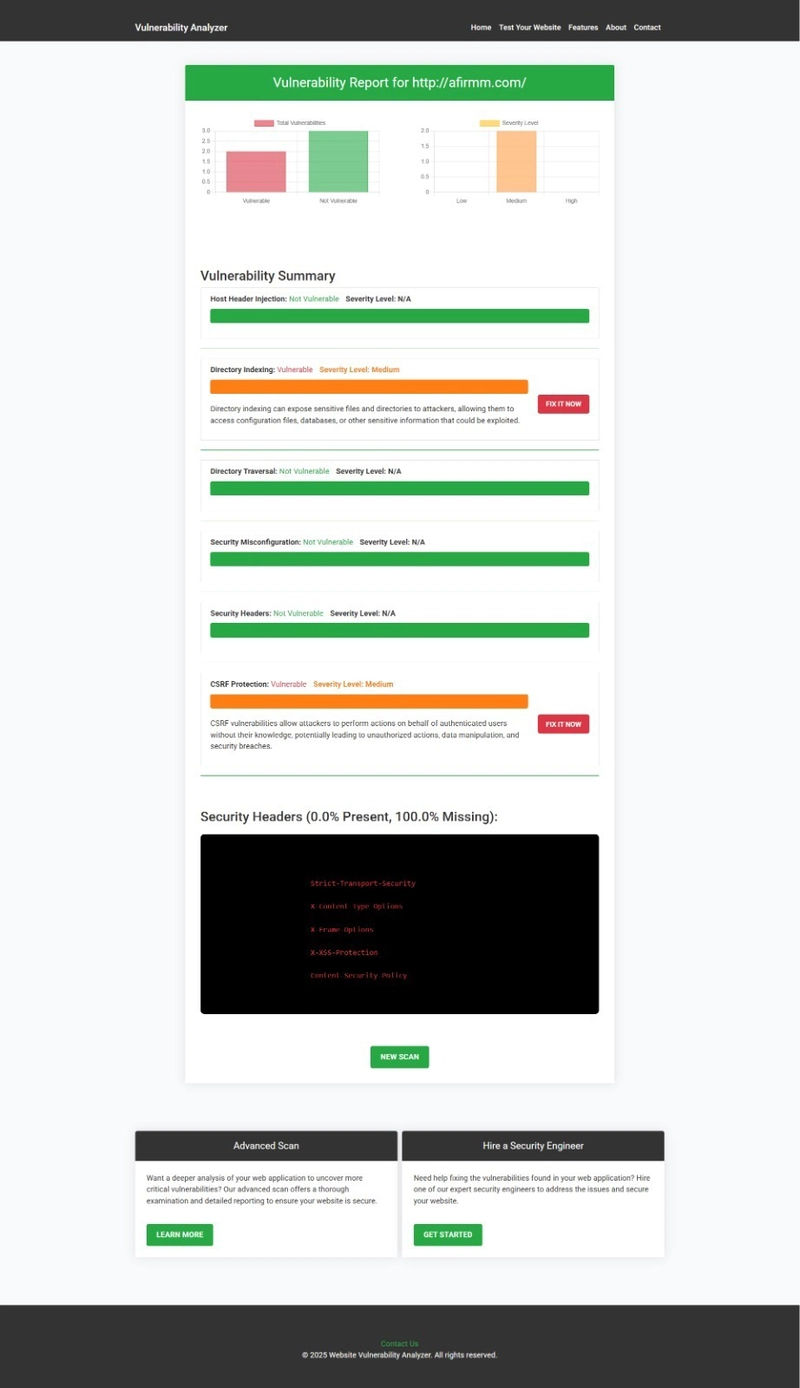 An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Try it now: 👉 https://free.pentesttesting.com/
📚 Related Reading
Want more deep dives into web app security and Symfony best practices? Check out our other blog posts at Pentest Testing Corp.
🔁 Final Thoughts
Sensitive data exposure in Symfony is often unintentional but devastating. Luckily, it's preventable with awareness, secure coding practices, and regular vulnerability assessments.
Don’t wait for a breach — run a Website Security Check on your site with our free tool and tighten your Symfony configurations today!




Top comments (0)