In my last post I discussed my tips for tracking and forecasting Amazon Bedrock costs on the management console 👇🏼
and after some discussions with readers on and offline, folks were wondering how they could also limit a user's Bedrock access (to models, to features, etc) via IAM policies.
The intent here is to adhere to both organization security policies and to budget constraints for developers experimenting and using AWS.
Let's jump in and see how this can be done 🤘🏼
Refresher on IAM
I hope if you're reading this you're intimately familiar with AWS IAM or Identity Access Management, as it's the foundation for controlling access to AWS resources. From authentication to authorization, IAM provides the necessary infrastructure to get this done.
You might be familiar with Amazon Bedrock access by way of the managed IAM policy AmazonBedrockFullAccess which provides users with unrestricted access to the entire suite of features available within the Bedrock service.
⚠️ This doesn't inherently mean access to all foundation models (FMs) by default. A user will still need to request access to FMs and accept EULAs to use models within Bedrock.
The practice of having users inherit a managed FullAccess policy is what we want to prevent for the purposes of this use case (and in general to adhere to AWS best practices for least privilege permissions).
Putting it all together
The behavior I want to demonstrate is a user having restricted access to Bedrock in order to prevent surprise usage spikes from simple mistakes- like using a model that management has deemed "too expensive," using features not approved, or exceeding use of a particular model.
For this demonstration I have created a user in IAM Identity Center . To prevent UI errors from the Bedrock console, at the time of creation this user is given the managed AmazonBedrockReadOnly policy. This will help prevent listing and reading errors in the UI as I click through. You can inspect the full details of that policy here.
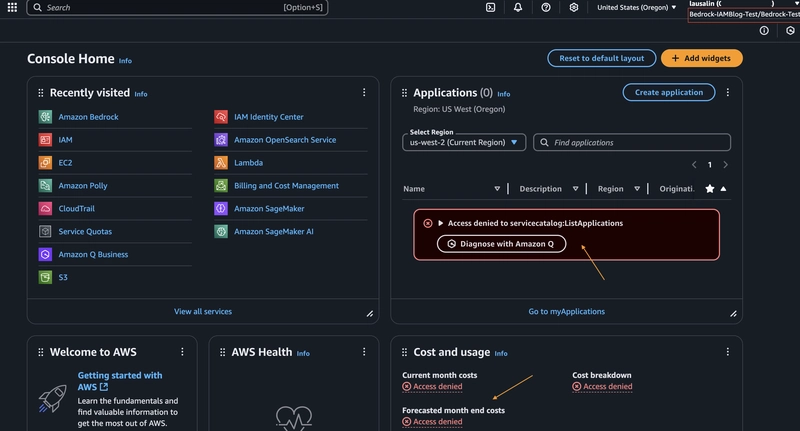
In the console, I can test whether this user is functional by logging into the identity center access portal for my user Bedrock-Test.
With only this policy attached, upon logging in I cannot use any AWS services.
⚠️ A reminder, if you're not able to access FMs, a user has to first request access and accept EULAs before attempting to use any models within Bedrock.
I test this by attempting to chat with a model in the playground.
As we further scope this policy, I want to allow a user to experiment with Bedrock only on the console playground and only with a certain model. I do this by listing the specific actions I want to allow and on Anthropic's Claude Opus model as the only resource.
⚠️ Before using any of these sample policies confirm you have permission to test IAM policies in your organization, and are working in a controlled environment (i.e., not prod). These IAM policies have been generated with Q Developer as a demonstration and should be subject to additional review before utilization. Note that this policy is scoped to a single account and thus requires an account ID.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "BedrockPlaygroundOnlyAccess",
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel",
"bedrock:InvokeModelWithResponseStream"
],
"Resource": [
"arn:aws:bedrock:*:*:foundation-model/anthropic.claude-3-opus-20240229-v1:0",
"arn:aws:bedrock:*:<Account ID>:inference-profile/*"
]
}
]
}
Limiting use of features
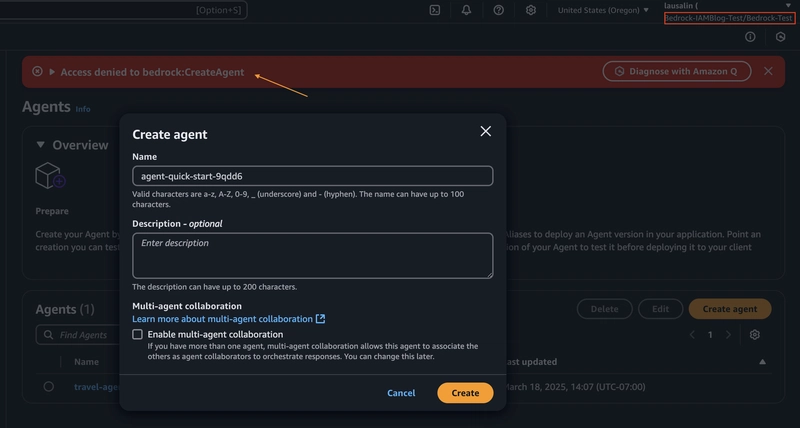
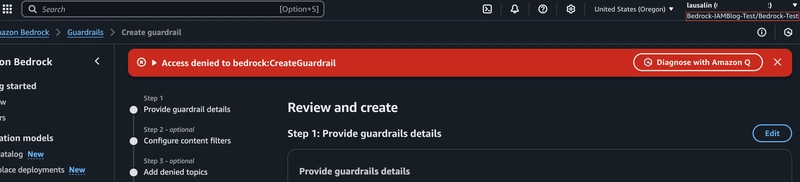
To confirm I only have access to the playground and no other features of Bedrock, I try creating a Bedrock Agent and a Bedrock Guardrail and see that I am denied access to both while under this user.
Limiting use of models
In this example I want to allow a user to have the same access above, but they should also be allowed to use the DeepSeek-R1 model in the playground. To do this, I add the JSON below to the policy I used previously. I indicate the behavior by allowing the action explicitly and using the ARN of the model in the resource field.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "BedrockPlaygroundOnlyAccess",
"Effect": "Allow",
"Action": [
"bedrock:InvokeModel",
"bedrock:InvokeModelWithResponseStream"
],
"Resource": [
"arn:aws:bedrock:*:*:foundation-model/anthropic.claude-3-opus-20240229-v1:0",
"arn:aws:bedrock:*:*:foundation-model/deepseek.r1-v1:0",
"arn:aws:bedrock:*:<Account ID>:inference-profile/*"
]
}
]
}
When I try the same prompt above but with the DeepSeek-R1 model, I can see my access is also allowed, and the query is processed.
Limiting use for a model
After some investigating, it seems there isn't currently a way to do this via IAM policies for Bedrock. At the time of writing, there is no direct IAM condition that limits the number of API calls or tokens for this use case. There may be other ways to tackle this via a combination of AWS Service Quotas and/or AWS Budgets, but I'll have to look into that for another day.
Leave a comment if you've explored this challenge or have some ideas about what a stopgap is for limiting Bedrock use on a per-model call/token basis.
Takeaways 💡
1/ To ensure best practices are followed, the AWS recommendation is to use Identity Center to manage authentication via existing IdP when possible.
2/ You can use IAM Access Analyzer during policy creation to review for various aspects like validating grammar and best practices. (You can locate these findings at the bottom of the JSON creation pane on the console)
3/ There are still some challenges in limiting API calls directly for Bedrock. The service team is aware of this limitation and actively working on a solution.
Additional Resources 📚










Top comments (0)